
CryptoLocker malware demands bitcoin ransom
A piece of malware is currently terrorising computer users by encrypting their data and charging a ransom – in fiat currency or bitcoins – to decrypt the information.
Called CryptoLocker, the ransom malware is contained within phishing emails, so it infects a users computer when they open an attachment in one of these messages.
Yuval Ben-Itzhak, CTO at security software company AVG, said: "Ransom malware has been around in different variations since the early 1990’s."
He went on to explain that a victim of the malware would typically receive an email that pretends to be from a well-known brand such as Fedex, UPS and DHS and claims to be related to a customer support issue.
"The email would have a zip file attachment which contains the executable code for the malware disguised as a PDF file. If the user clicks on this PDF icon, it infects the computer as soon as it opens," Ben-Itzhak added.
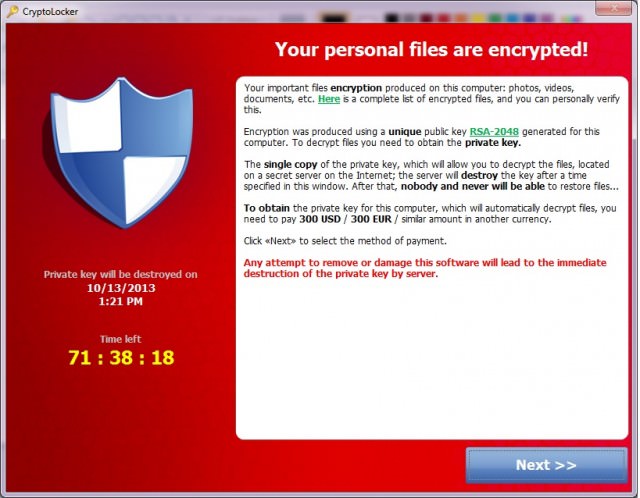
Once a computer is infected, a message is displayed on the screen, stating: "To obtain the private key for this computer, which will automatically decrypt files, you need to pay 300 USD / 300 EUR / similar amount in another currency."
Users are given a choice of payment method, but CryptoLocker describes bitcoin as the "most cheap option" and asks for 2 BTC.
CryptoLocker-malware
Forum members have been sharing the information they know about CryptoLocker on reddit, discussing its features, how it is spread and which antivirus software catches it.
A roundup post by forum member 'bluesoul' informs that there is a version of CryptoLocker that demands $100 and another that asks for $300. It also reveals that the victim's files will be encrypted before the warning message displays on their screen.
"I thought it was worth mentioning that by the time the notification pops up, it's already encrypted everything. It's silent until the job is done," bluesoul's forum post reads.
recently published a post on its blog stating that it is seeing an influx of customers who are trying to buy bitcoins to pay to those behind the CryptoLocker malware.
The UK bitcoin exchange said it is not selling coins to anyone who need them for Crypto-Locker.
"Knowingly accepting money so that the coins may be sent to the criminals would turn the service into a money laundering operation, encourage the criminals to take this to a higher level, not to mention the sellers could easily get tangled up in a police investigation or get their bank accounts frozen," Bitbargain's blog post explains.
AVG's Ben-Itzhak said users can minimise the risk of their computer becoming infected by this or other types of malware by having an active and up-to-date antivirus program on their PC.
Bitbargain, however, offered this advice: "The moral of the story is: always have backups, always update your software (especially Adobe Reader which has a very bad history of vulnerabilities resulting in code execution), and do not open e-mail attachments unless you know who sent it."
Have you been affected by CryptoLocker? Let us know your thoughts on this malware in the comments.
Image credit: Peas via Ars Technica
DISCLOSURE
The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. As part of their compensation, certain CoinDesk employees, including editorial employees, may receive exposure to DCG equity in the form of stock appreciation rights, which vest over a multi-year period. CoinDesk journalists are not allowed to purchase stock outright in DCG.


