Google patches Android flaw that led to bitcoin heist
Google has released an advisory to developers on how to deal with the recently discovered flaw in Android that led to the theft of thousands of dollars in bitcoin from mobile app wallets.
The [then] potential flaw was first reported on the Bitcoin forum, where it was reported that over 55 BTC had been stolen from multiple users to the same bitcoin address. The forum user also reported that the (software) clients that had been stolen from had signed the transaction messages with the same random number. This in turn led some to believe that Android's pseudo random number generator (PRNG) was not being properly initialised.
When transaction messages are signed, they are signed with a combination of one's private key and a random number. The random number's purpose is to conceal the value of the private key. If the same random number is used more than once, the private key can be deduced.

blockchain android update
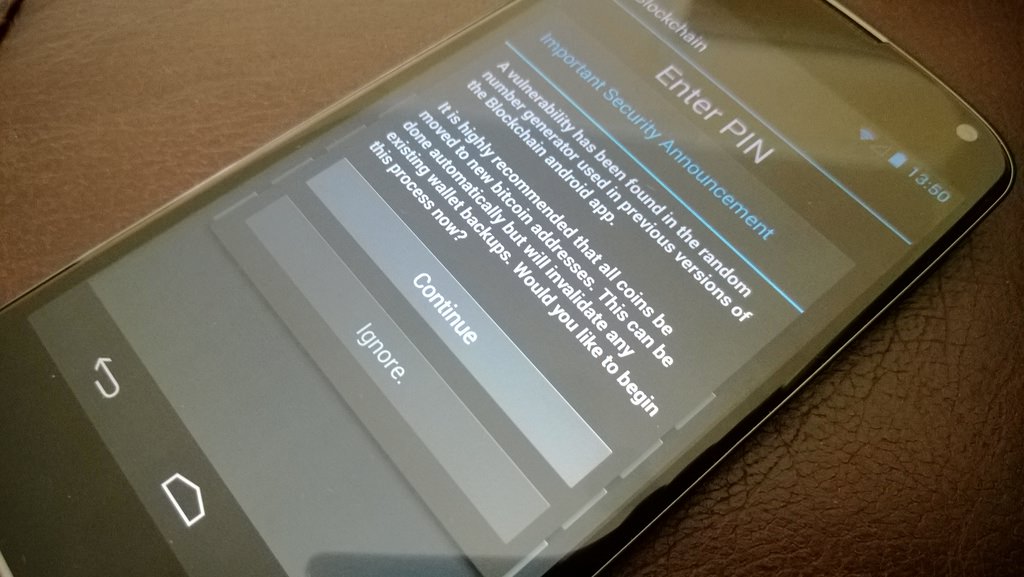
Bitcoin developers issued an alert about this within 24 hours of the forum post. In which it named some of the affected apps: Bitcoin Wallet, Blockchain.info wallet, BitcoinSpinner and Mycelium Wallet. Furthermore, it confirmed that updates had been prepared for the named applications. Indeed, we can independently verify that at least the Blockchain.info app had been updated prior to the time of writing.
The Bitcoin developers went on to advise that users make sure they update their apps as soon as possible, and in the meantime to move coins away to an alternative wallet.
More recently, Google come forward to make a statement on its Android Developer blog. It confirmed that applications using the Java Cryptography Architecture (JCA) were not receiving cryptographically strong values due to improper initialization (i.e. a "seed value"). It also confirmed that the PRNG of Android's SSL and TLS signing was not affected by this flaw.
Fortunately there is something that developers can (and have) done now to deal with the problem, as the underlying PRNG of the JCA can be explicitly initialised with a better-than-default seed value.
Furthermore, the Android developer team has issued a fix to the Open Handset Alliance (OHA) so that OEMs can implement the fix into their Android distributions. However, any Android update has to pass through OEM testing, and then go through operator approval. Therefore, the patch will likely take a long time to trickle down to end users.
Bitcoin expert and information security professional Vladimir Marchenko reminded users that flaws in software do happen, and that they should always be mindful of applying security patches and software updates in a timely manner. He also spoke to the strength of the Bitcoin team:
Marchenko went on to give the following cautionary note: "As a general note it might be unwise to use mobile phones to store large amounts of bitcoins. The mobile devices are, however, extremely convenient in day-to-day use of bitcoin and having small amounts stored there while larger amounts are stored more securely elsewhere makes sense.
"Just like people have savings accounts and current accounts in banks, users should separate long-term storage of larger amounts of bitcoins and more convenient storage of smaller amounts for day-to-day use. This reduces the amount of assets at risk and therefore overall risk, while providing a reasonable level of convenience."
DISCLOSURE
The leader in news and information on cryptocurrency, digital assets and the future of money, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. CoinDesk is an independent operating subsidiary of Digital Currency Group, which invests in cryptocurrencies and blockchain startups. As part of their compensation, certain CoinDesk employees, including editorial employees, may receive exposure to DCG equity in the form of stock appreciation rights, which vest over a multi-year period. CoinDesk journalists are not allowed to purchase stock outright in DCG.

